How to Install Let’s Encrypt Wildcard SSL For Your Domain – ACME v2
Let’s Encrypt is a free, automated, and open certificate authority (CA), run for the public’s benefit. It is a service provided by the Internet Security Research Group (ISRG). Basically they provide hassle free no cost ssl for your domains, recently Let’s Encrypt introduced WIldcard ssl for your domain, now you can use wildcard free ssl for your domain and for multiple subdomain with just single SSL cert (no need to issue certs for every subdomain) even WordPress MultiSite (https ) run fine with it.
The key principles behind Let’s Encrypt are:
- Free: Anyone who owns a domain name can use Let’s Encrypt to obtain a trusted certificate at zero cost.
- Automatic: Software running on a web server can interact with Let’s Encrypt to painlessly obtain a certificate, securely configure it for use, and automatically take care of renewal.
- Secure: Let’s Encrypt will serve as a platform for advancing TLS security best practices, both on the CA side and by helping site operators properly secure their servers.
- Transparent: All certificates issued or revoked will be publicly recorded and available for anyone to inspect.
- Open: The automatic issuance and renewal protocol will be published as an open standard that others can adopt.
- Cooperative: Much like the underlying Internet protocols themselves, Let’s Encrypt is a joint effort to benefit the community, beyond the control of any one organization.
In this tutorial we’ll cover and Issue Wildcard Let’s Encrypts ssl for domain. This tutorial will work on several Linux distributions like Redhat, CentOS (el6, el7), Ubuntu, fedora etc. Let’s get started :-
Step 1
Change the directory to root :
cd /root
Step 2
For Let’s Encrypt to work we need ACME client protocol (also ensure cURL is installed) :
yum install socat curl https://get.acme.sh | sh /root/.acme.sh/acme.sh --set-default-ca --server letsencrypt
OR
yum install socat git git clone https://github.com/Neilpang/acme.sh.git cd ./acme.sh ./acme.sh --install /root/.acme.sh/acme.sh --set-default-ca --server letsencrypt
you’ll see it will download and add acme script.
Step 3
Issuing wildcard ssl for domain via command line :
this command will ask you to add some dns TXT records for validation purpose it is necessory to add those record otherwise cert issuing will fail.
acme.sh --issue -d mysterydata.com -d *.mysterydata.com --dns --force
if you’re getting :
It seems that you are using dns manual mode. Read this link first: https://github.com/Neilpang/acme.sh/wiki/dns-manual-mode
then run this command (recommended):
acme.sh --issue -d mysterydata.com -d *.mysterydata.com --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please
* replace mysterydata.com with your domain name
after you run this command it will ask you to add TXT record like below :
[root@demo ~]# acme.sh --issue -d mysterydata.com -d *.mysterydata.com --dns --force [Wed Mar 14 10:18:10 EDT 2018] Registering account [Wed Mar 14 10:18:13 EDT 2018] Registered [Wed Mar 14 10:18:13 EDT 2018] ACCOUNT_THUMBPRINT='MO7DtJidci1tp4CNPDUbQA0_jPjR3tKy8uQE-Q_Bb7k' [Wed Mar 14 10:18:13 EDT 2018] Creating domain key [Wed Mar 14 10:18:13 EDT 2018] The domain key is here: /root/.acme.sh/mysterydata.com/mysterydata.com.key [Wed Mar 14 10:18:13 EDT 2018] Multi domain='DNS:mysterydata.com,DNS:*.mysterydata.com' [Wed Mar 14 10:18:13 EDT 2018] Getting domain auth token for each domain [Wed Mar 14 10:18:15 EDT 2018] Getting webroot for domain='mysterydata.com' [Wed Mar 14 10:18:15 EDT 2018] Getting webroot for domain='*.mysterydata.com' [Wed Mar 14 10:18:15 EDT 2018] Add the following TXT record: [Wed Mar 14 10:18:15 EDT 2018] Domain: '_acme-challenge.mysterydata.com' [Wed Mar 14 10:18:15 EDT 2018] TXT value: 'YABz8SMXk_qqrIrUgx5_DWSjBUSuDsdvIxJ4RIEwMUQ' [Wed Mar 14 10:18:15 EDT 2018] Please be aware that you prepend _acme-challenge. before your domain [Wed Mar 14 10:18:15 EDT 2018] so the resulting subdomain will be: _acme-challenge.mysterydata.com [Wed Mar 14 10:18:15 EDT 2018] Add the following TXT record: [Wed Mar 14 10:18:15 EDT 2018] Domain: '_acme-challenge.mysterydata.com' [Wed Mar 14 10:18:15 EDT 2018] TXT value: 'j4x7b-mzV7cCYCHT_LfLaAW0wDYMeeYayMMvindIGko' [Wed Mar 14 10:18:15 EDT 2018] Please be aware that you prepend _acme-challenge. before your domain [Wed Mar 14 10:18:15 EDT 2018] so the resulting subdomain will be: _acme-challenge.mysterydata.com [Wed Mar 14 10:18:15 EDT 2018] Please add the TXT records to the domains, and retry again. [Wed Mar 14 10:18:15 EDT 2018] Please add '--debug' or '--log' to check more details. [Wed Mar 14 10:18:15 EDT 2018] See: https://github.com/Neilpang/acme.sh/wiki/How-to-debug-acme.sh
You can see the TXT records are already mentioned here as :
[Wed Mar 14 10:18:15 EDT 2018] Add the following TXT record: [Wed Mar 14 10:18:15 EDT 2018] Domain: '_acme-challenge.mysterydata.com' [Wed Mar 14 10:18:15 EDT 2018] TXT value: 'YABz8SMXk_qqrIrUgx5_DWSjBUSuDsdvIxJ4RIEwMUQ' [Wed Mar 14 10:18:15 EDT 2018] Add the following TXT record: [Wed Mar 14 10:18:15 EDT 2018] Domain: '_acme-challenge.mysterydata.com' [Wed Mar 14 10:18:15 EDT 2018] TXT value: 'j4x7b-mzV7cCYCHT_LfLaAW0wDYMeeYayMMvindIGko'
Now you need to add this records don’t add this eg. use the actual TXT record which shown on your shell console (A records DNS and TXT record):
A record _acme-challenge.mysterydata.com poiniting to the server IP
TXT record _acme-challenge.mysterydata.com
value : “YABz8SMXk_qqrIrUgx5_DWSjBUSuDsdvIxJ4RIEwMUQ”
TXT record _acme-challenge.mysterydata.com
value : “j4x7b-mzV7cCYCHT_LfLaAW0wDYMeeYayMMvindIGko”
Add wildcard dns :
*.mysterydata.com. 14400 IN A 107.152.32.123
* replace mysterydata.com with your domain name
ultimately DNS config will look like this :
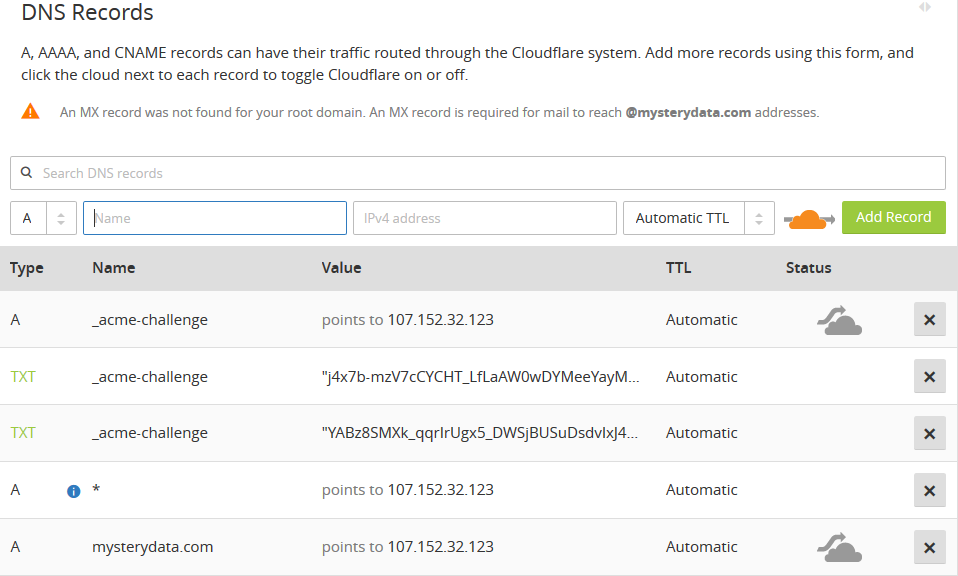
Step 4 :
After adding the DNS wait for the DNS propagation and run this command to issue the certs :
acme.sh --renew -d mysterdata.com -d *.mysterdata.com --dns --force
* replace mysterydata.com with your domain name
Or (recommeneded) :
acme.sh --renew -d mysterydata.com -d *.mysterydata.com --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please
* replace mysterydata.com with your domain name
this is dns manual mode, it can not be renewed automatically. you will have to add a new txt record to your domain by your hand when you renew your cert.
you can check TXT record updated or not via this command :
dig -t txt dig -t txt _acme-challenge.mysterydata.com
* replace mysterydata.com with your domain name
all set, you’ll see certs are now issued successfully. Cert, Chain file and Private Key will be saved under :
/root/.acme.sh/yourdomain.com
with name :
mysterydata.com.cer <<=== Cert file
mysterydata.com.key <<=== Private Key
fullchain.cer <<=== CA Chain file/bundle file
Now you can use this file in ssl vhost just update/add the path (you can search on google how to add ssl vhost for nginx and Apache) :
Also ensure you’ve enabled wildcard vhost for apache or nginx whatever your main webserver is. Or use multiple vhost with same cert paths as mentioned below.
apache :
SSLCertificateFile /root/.acme.sh/mysterydata.com/mysterydata.com.cer SSLCertificateKeyFile /root/.acme.sh/mysterydata.com/mysterydata.com.key SSLCertificateChainFile /root/.acme.sh/mysterydata.com/fullchain.cer
nginx :
ssl_certificate /root/.acme.sh/mysterydata.com/fullchain.cer; ssl_certificate_key /root/.acme.sh/mysterydata.com/mysterydata.com.key;
* replace mysterydata.com with your domain name
Step 5 :
To renew the certs you just need to run this command ensure you run this command in 90 days, update TXT dns record if shown as mentioned above in step 3:
acme.sh --issue -d mysterydata.com -d *.mysterydata.com --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please
or
acme.sh --renew -d mysterdata.com -d *.mysterdata.com --dns --force --yes-I-know-dns-manual-mode-enough-go-ahead-please
* replace mysterydata.com with your domain name
Automatic Cert Renew (only if you used Auto DNS add via API):
For more info about DNS api and how to do it visit this offiial page : https://github.com/Neilpang/acme.sh/tree/master/dnsapi Auto renew let’s encrypt certs via Cron job : add this daily cron for the auto renew check :
0 0 * * * "/root/.acme.sh"/acme.sh --cron --home "/root/.acme.sh" > /dev/null
Thats it you’ve enable Let’s encrypt wildcard SSL, Let me know if you find this article helpful 🙂