Get A+ Score Rating with SSLLabs Qualys in CWP – Control web panel
In this tutorial we’ll do config in cwp so we can get SSL A+ Score Rating in SSLLabs – Qualys. Upon many request by the visitors and members I’m posting this easy tutorial. This guide will help you to achieve A+ ssl rating in ssl labs Qualys so you’ll get high-level of ssl security, as well as enhance the security of your IT/eCommerce business and building customer confidence and loyalty.
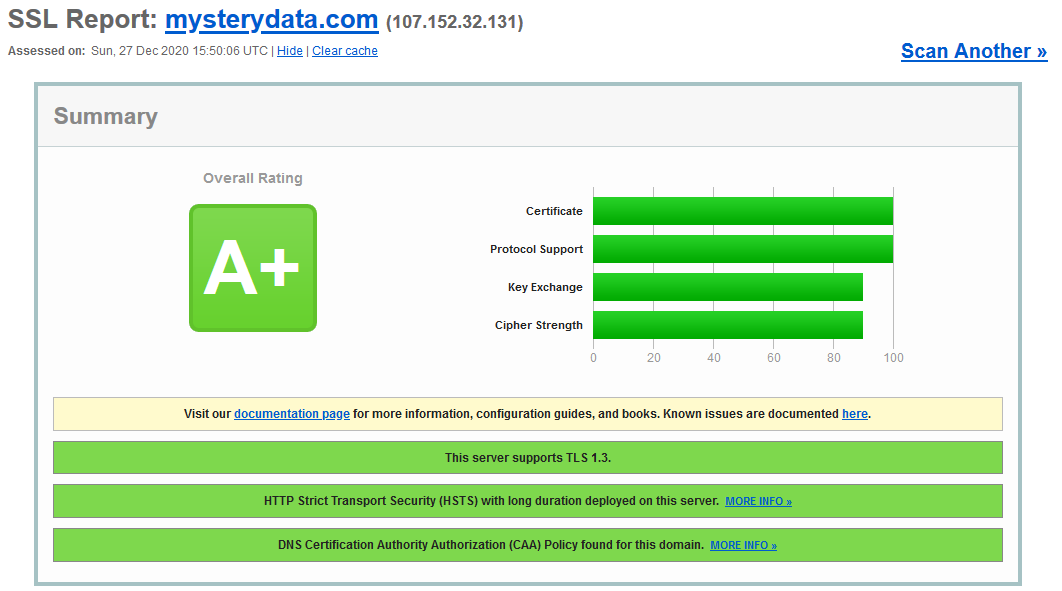
I’ve an article here for Webserver basis config https://blog.alphagnu.com/how-to-get-a-score-rating-in-ssllabs-qualys/ since CWP is different and works with template many users are trouble achieve this score, below are the steps mentioned which you need to follow one by one
Ensure you logged in as root in ssh/terminal
FOR NGINX (proxy/main/fpm) :
Step 1 :
Download this template to your server :
cd /usr/local/cwpsrv/htdocs/resources/conf/web_servers/vhosts wget --no-cache https://blog.alphagnu.com/upload/nginx-Aplus.zip unzip -o nginx-Aplus.zip rm -rf nginx-Aplus.zip
Step 2 :
Change the ssl protocol to only use TLS 1.2 :
sed -r -i 's/\b(TLSv1 |TLSv1.1 )\b//g' /etc/nginx/nginx.conf /etc/nginx/conf.d/*.conf /etc/nginx/conf.d/vhosts/*.conf /usr/local/cwpsrv/htdocs/resources/conf/web_servers/main/nginx/conf/nginx.conf
***When you rebuild webserver or vhost from CWP ensure you run this command again.
Extra:
After running the above command lock this files if you don’t change nginx main config and Hostname of the server :
chattr +i /etc/nginx/conf.d/hostname-ssl.conf /etc/nginx/nginx.conf
If you want to change nginx main conf or change the server hostname just unlock this files and then rebuild webserver config or vhost :
chattr -i /etc/nginx/conf.d/hostname-ssl.conf /etc/nginx/nginx.conf
***after edit and webserver rebuild or vhost rebuild just lock the files again.
Step 3 :
Apply the templates new templates will appear as “-Aplus” word added.
***Remember if you choose any other template for the domain with tls 1 and tls 1.1 protocol active then A + score will downgrade to lower score hence it is recommended to use the A+ templates for all of your domain and SANs.
CLICK here to view Full size : Image
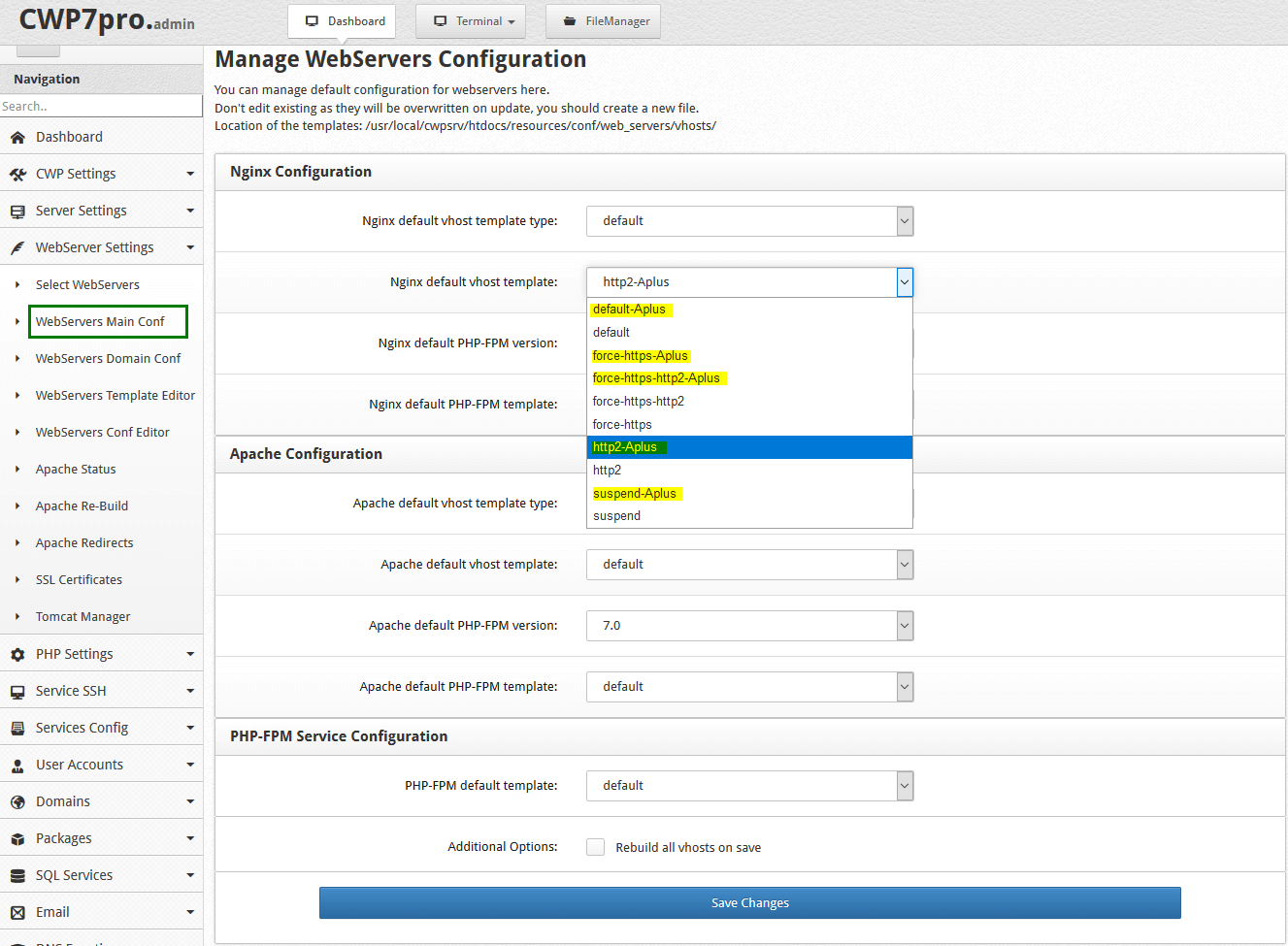
If you’ve per “webserver domain config” enabled for per user domain then you need to choose this templates there too.
For APACHE only webserver (php-cgi/fpm/proxy) follow this guide for apache :
Edit :
/usr/local/apache/conf.d/ssl.conf
ensure you’ve disabled TLS 1.0 and TLS 1.1 ssl protocol and add this ciphers :
<IfModule !ssl_module>
LoadModule ssl_module modules/mod_ssl.so
</IfModule>
Listen 443
SSLProtocol all -SSLv2 -SSLv3 -TLSv1 -TLSv1.1
SSLHonorCipherOrder on
SSLCipherSuite "EECDH+ECDSA+AESGCM:EECDH+aRSA+AESGCM:EECDH+ECDSA+SHA384:EECDH+ECDSA+SHA256:EECDH+aRSA+SHA384:EECDH+aRSA+SHA256:EECDH+aRSA!RC4:EECDH:!RC4:!aNULL:!eNULL:!LOW:!3DES:!MD5:!EXP:!PSK:!SRP:!DSS"** tally the changes basically you only need to edit “SSLProtocol” and “SSLCipherSuite
and restart apache :
systemctl restart httpd
now add HSTS header in domain .htaccess :
Header always set Strict-Transport-Security "max-age=31536000"
Extra work :
you need to also add Certification Authority Authorization (CAA) dns record for more security read here LINK
Like you can add CAA dns who you want to give permission to issue certs :
mysterydata.com. 300 IN CAA 0 issue "digicert.com" mysterydata.com. 300 IN CAA 0 issuewild "digicert.com"
mysterydata.com. 300 IN CAA 0 issuewild "letsencrypt.org" mysterydata.com. 300 IN CAA 0 issue "letsencrypt.org"
mysterydata.com. 300 IN CAA 0 issuewild "comodoca.com" mysterydata.com. 300 IN CAA 0 issue "comodoca.com"
mysterydata.com. 300 IN CAA 0 issuewild "globalsign.com" mysterydata.com. 300 IN CAA 0 issue "globalsign.com"